hello friends! new(ish)!
SSH: Difference between revisions
>Tinfoil-hat No edit summary |
m (Changed the guide to use the native Windows OpenSSH server instead of PuTTY) |
||
| Line 2: | Line 2: | ||
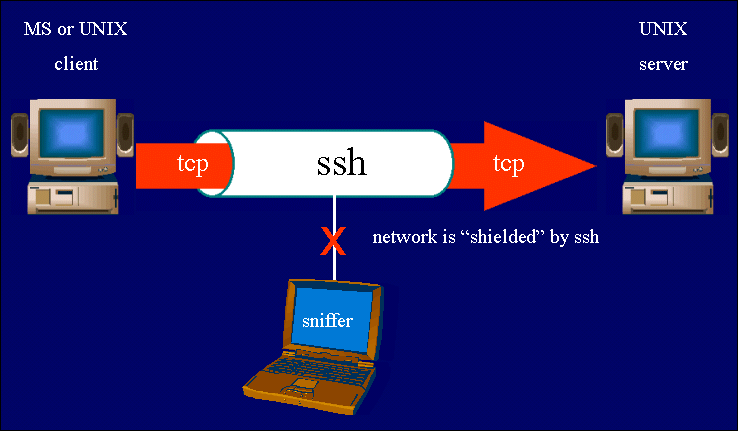
SSH ('''S'''ecure '''Sh'''ell) is a network protocol that allows secure communications between two devices. What that means for the average /g/entleman is that you can run SSH on a server and then securely log in to your server anywhere when properly configured. In simpler terms, you can run your server via command-line anywhere. You can also browse the internet with your server's connection, effectively bypassing the filters many underageb& have on their school networks. SSH is free software with utilities on all major operating systems. | SSH ('''S'''ecure '''Sh'''ell) is a network protocol that allows secure communications between two devices. What that means for the average /g/entleman is that you can run SSH on a server and then securely log in to your server anywhere when properly configured. In simpler terms, you can run your server via command-line anywhere. You can also browse the internet with your server's connection, effectively bypassing the filters many underageb& have on their school networks. SSH is free software with utilities on all major operating systems. | ||
==Connecting to an SSH Server== | ==Connecting to an SSH Server== | ||
*On Windows, make sure to [https://learn.microsoft.com/en-us/windows/terminal/tutorials/ssh#access-windows-ssh-client-and-ssh-server enable SSH], if it isn't already on. | |||
*[http://www.openssh.org/manual.html Read the fucking manual.] | *[http://www.openssh.org/manual.html Read the fucking manual.] | ||
*For setting up your own SSH server on GNU/Linux or *BSD, check the [[Setting up a Server|local article on doing so securely]]. Virtually no modern distro ships without an SSH client. [[RTFM|Check your distribution's documentation.]] | * For setting up your own SSH server on GNU/Linux or *BSD, check the [[Setting up a Server|local article on doing so securely]]. Virtually no modern Linux distro ships without an SSH client. [[RTFM|Check your distribution's documentation.]] | ||
*If your distro starts an ssh daemon by default, it's an insecure piece of shit. | *If your distro starts an ssh daemon by default, it's typically an insecure piece of shit. | ||
==What Can I Do?== | ==What Can I Do?== | ||
*Browse the server via command-line (I hope you know UNIX shell commands) | *Browse the server via command-line (I hope you know UNIX shell commands) | ||
*Transfer files between the client and the server (You can use SSH, but there are better tools for the job) | *Transfer files between the client and the server (You can use SSH, but there are better tools for the job) | ||
*Browse using the server's internet ([http://lifehacker.com/237227/geek-to-live--encrypt-your-web-browsing-session-with-an-ssh-socks-proxy Read this] | *Browse using the server's internet ([http://lifehacker.com/237227/geek-to-live--encrypt-your-web-browsing-session-with-an-ssh-socks-proxy Read this]) | ||
*Other stuff that I don't know. | *Other stuff that I don't know. | ||
==Generating an SSH key pair | ==Generating an SSH key pair== | ||
Most modern SSH setups will require you to use a key pair to connect. It works by generating a public and a private key, optionally protected by a strong passphrase. You then place the public key on the remote system, the private key is stored somewhere safe, where unauthorized people can't access it. | |||
It works by generating a public and a private key, optionally protected by a strong passphrase. You then place the public key on the remote system, the private key is stored somewhere safe, where unauthorized people can't access it. | |||
See the following link on how to generate an SSH key pair: | See the following link on how to generate an SSH key pair: | ||
| Line 57: | Line 43: | ||
<b> Examples</b> | <b> Examples</b> | ||
Forwarding | Forwarding from port 8000 on the local system to the Web server (port 80) on Server: | ||
ssh -L 8000:localhost:80 server -N & | ssh -L 8000:localhost:80 server -N & | ||
| Line 96: | Line 82: | ||
helpdeskpc$ ssh user@vps -t ssh needsupportpcuser@localhost:2222 | helpdeskpc$ ssh user@vps -t ssh needsupportpcuser@localhost:2222 | ||
==Conclusion== | == Conclusion == | ||
Any /g/entleman who can leave a computer running 24/7 has no reason not to run an SSH server. Honestly, even some junk box will work just fine, no need to leave a gaming rig on to SSH. | Any /g/entleman who can leave a computer running 24/7 has no reason not to run an SSH server. Honestly, even some junk box will work just fine, no need to leave a gaming rig on to SSH. | ||
Latest revision as of 22:36, 7 December 2024
SSH (Secure Shell) is a network protocol that allows secure communications between two devices. What that means for the average /g/entleman is that you can run SSH on a server and then securely log in to your server anywhere when properly configured. In simpler terms, you can run your server via command-line anywhere. You can also browse the internet with your server's connection, effectively bypassing the filters many underageb& have on their school networks. SSH is free software with utilities on all major operating systems.
Connecting to an SSH Server
- On Windows, make sure to enable SSH, if it isn't already on.
- Read the fucking manual.
- For setting up your own SSH server on GNU/Linux or *BSD, check the local article on doing so securely. Virtually no modern Linux distro ships without an SSH client. Check your distribution's documentation.
- If your distro starts an ssh daemon by default, it's typically an insecure piece of shit.
What Can I Do?
- Browse the server via command-line (I hope you know UNIX shell commands)
- Transfer files between the client and the server (You can use SSH, but there are better tools for the job)
- Browse using the server's internet (Read this)
- Other stuff that I don't know.
Generating an SSH key pair
Most modern SSH setups will require you to use a key pair to connect. It works by generating a public and a private key, optionally protected by a strong passphrase. You then place the public key on the remote system, the private key is stored somewhere safe, where unauthorized people can't access it.
See the following link on how to generate an SSH key pair:
How to use ssh-keygen to generate a new SSH key | SSH.COM
Advanced Usage
SSH Tunnel
SSH-Tunnel Syntax:
ssh -L [bind_address:]port:host:port user@server ssh -R [bind_address:]port:host:port user@server
the option -L creates a local, and the Option -R a remote Port Forwarding. The encrypted tunnel is created always between Client and Server. The connection from "tunnel end" to host happens unencrypted, this is why you set it in most cases to localhost. Therefore localhost should not be confused with the local Computer. You have to see this localhost from server perspective, so the Server itself.
Die Option -L bzw. -R sets the direction. if you choose -L the direction is from your own Computer to the remote one, if you choose -R in the opposite direction. (you can think of it as normaL backwaRds.)
The first Port Argument is the entryport in the connection. You have to keep in mind, that the opening of a "privileged" port, so under 1024, only is allowed by root, so you should choose a higher one.
With the optional parameter bind_address you can seon which specific network address the connection should use, whereas localhost is default. A * or an empty bind_address-argument before the colon means, that the forwarding is on all Interfaces / Network Adresses. Probably whis will only work with IPv4 Adresses because the IPv6-Adresses aren't capable of beeing forwarded, Therefore you should use the Argument -4 .
The second port-parameter tells which Port tells, which port from host the tunneling should go on
Another useful argument is the option -N, which refuses a terminal-session, if you only want to use the Portforwarding to the remote systeme.
Examples
Forwarding from port 8000 on the local system to the Web server (port 80) on Server:
ssh -L 8000:localhost:80 server -N & netstat -anp --inet | egrep '(^Proto|8000)' Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN 10843/ssh fg ssh -L 8000:localhost:80 server -N [Strg-C] Killed by signal 2.
Same, but it isn't just a connection from local Host forwarded, but from all Interfaces (hint: you need to set the option - GatewayPorts ; use this option with caution!):
ssh -L *:8000:localhost:80 server -N -4 & netstat -anp --inet | egrep '(^Proto|8000)' Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN 10906/ssh
Reverse direction. You allow Users on the Server, via localhost:3306 to connect to the clients MySQL-Server:
ssh -R 3306:localhost:3306 server Last login: Sat Mar 11 23:24:20 2006 from 192.168.4.56 netstat -an --inet | egrep '(^Proto|3306)' Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN exit logout Connection to server closed.
Here you can see an example of a double SSH Reverse tunnel:
needsupportpc$ ssh -R 22:localhost:2222 user@vps helpdeskpc$ ssh user@vps -t ssh needsupportpcuser@localhost:2222
Conclusion
Any /g/entleman who can leave a computer running 24/7 has no reason not to run an SSH server. Honestly, even some junk box will work just fine, no need to leave a gaming rig on to SSH.